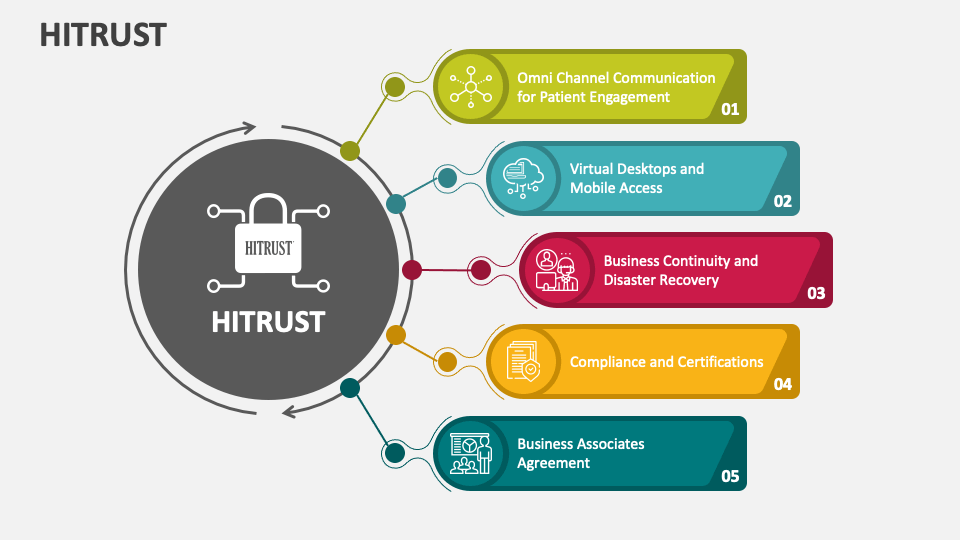
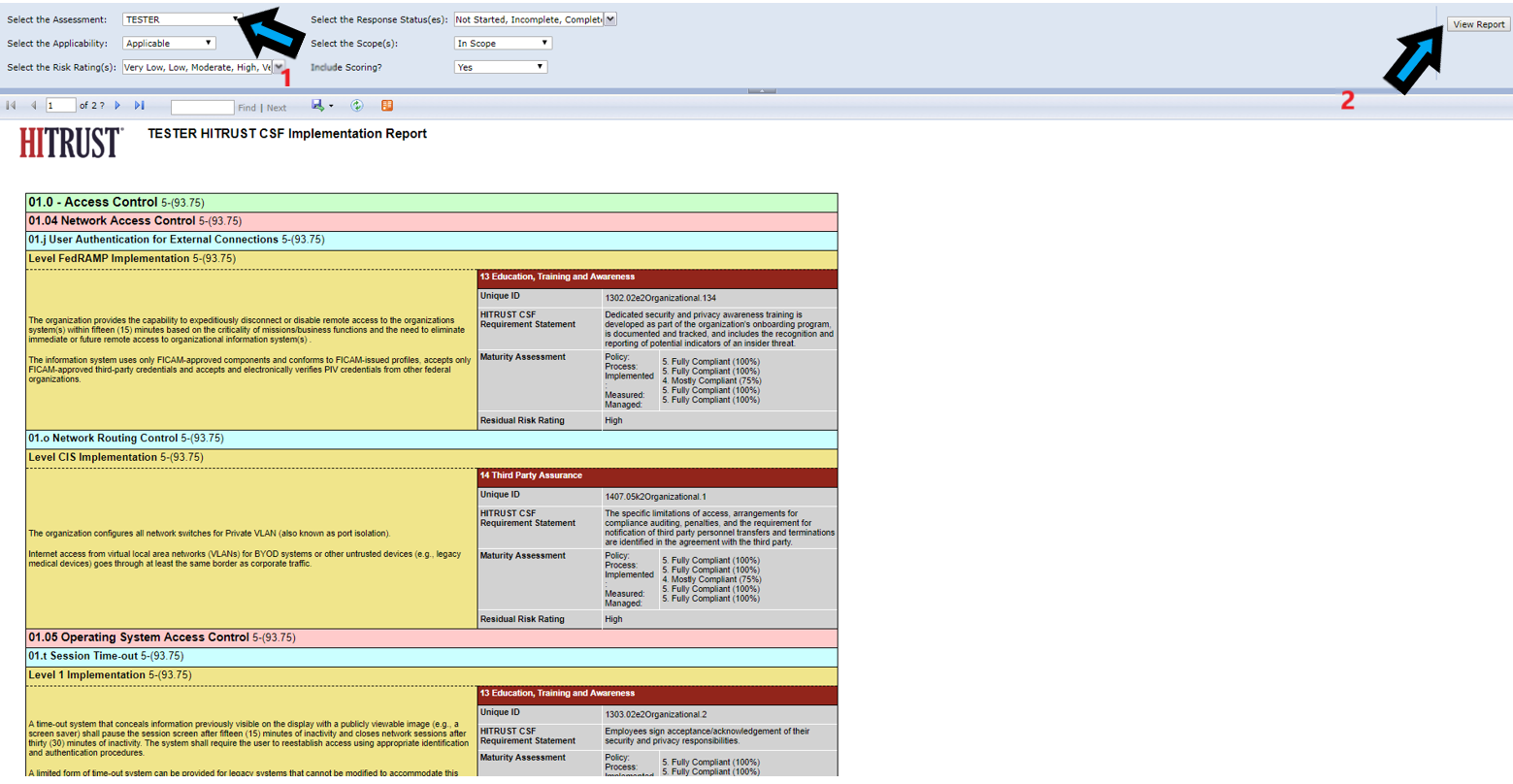
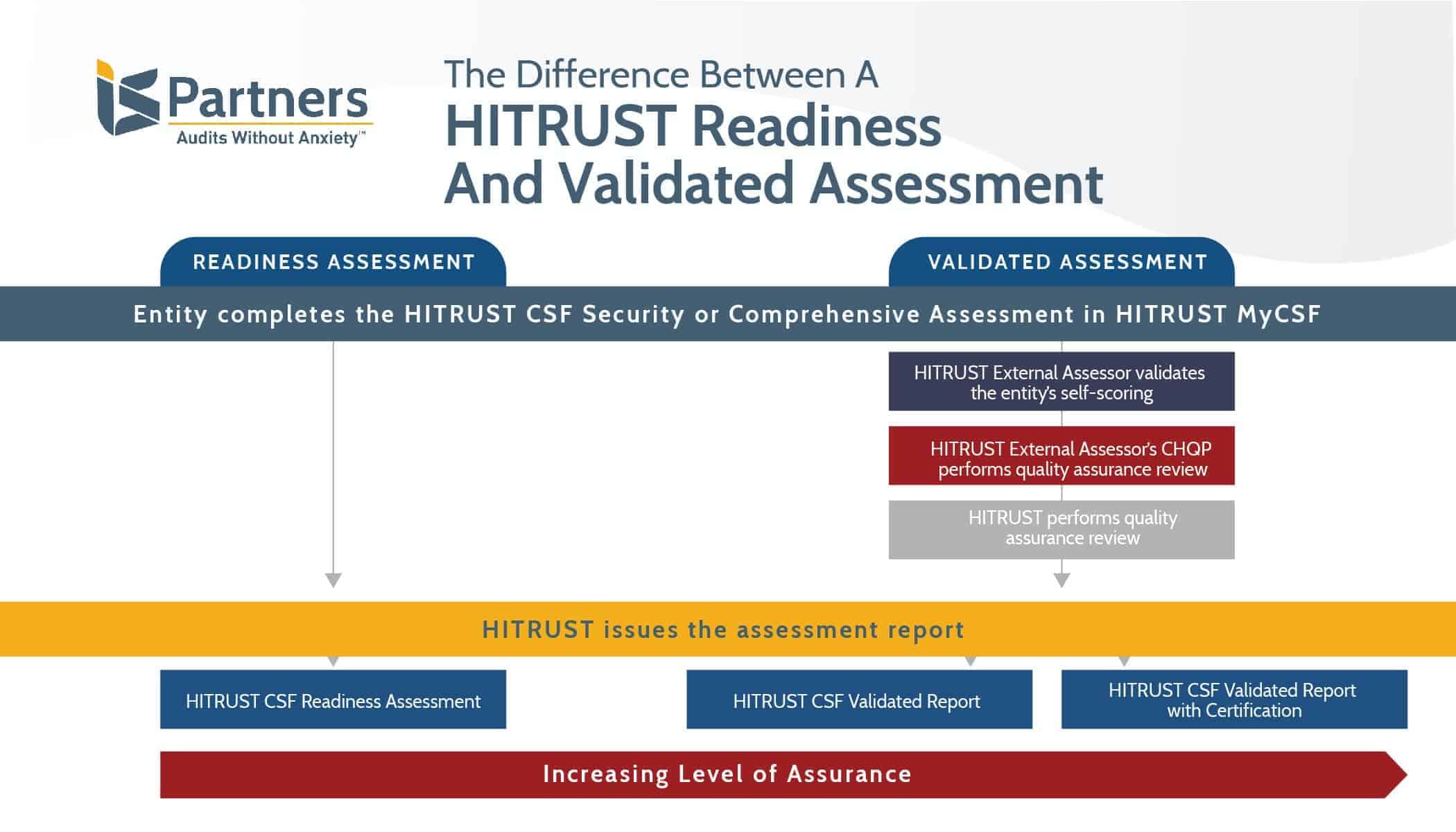
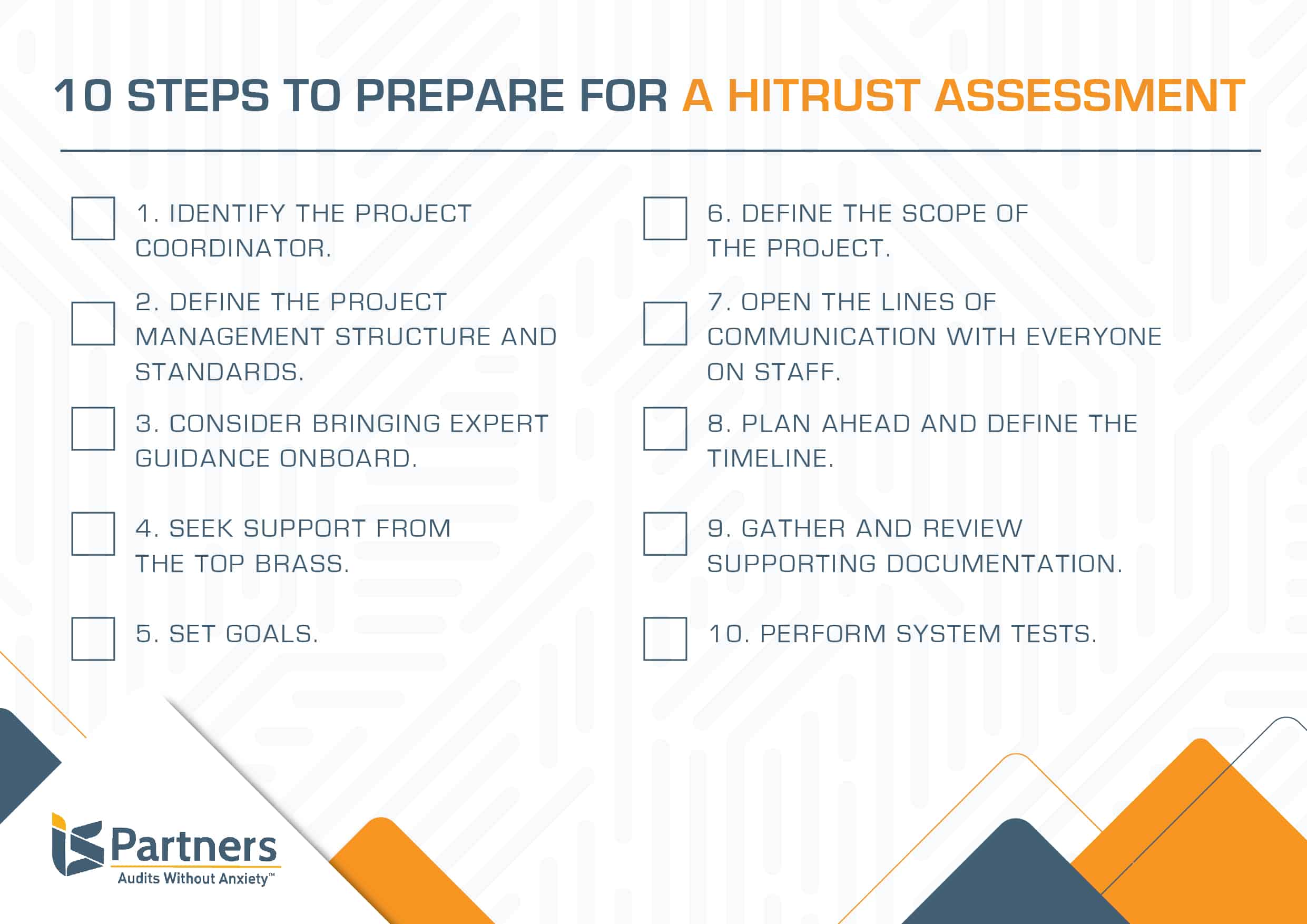
Hitrust Policy Templates - The following is a library of free information security policy templates that map to the hitrust common security framework, which in turn maps to a. We’ve outlined the requirements of hitrust policies and procedures, the audit process surrounding the advanced paper exercise, and what you can do to. This guide provides updated guidance for the assessment of hitrust csf control requirements using the hitrust csf control maturity model,. Cone health information and technology services is committed to the security of its assets, personnel, and. This checklist is designed to help ensure the consistency and quality of hitrust validated assessments and resulting reports.
This checklist is designed to help ensure the consistency and quality of hitrust validated assessments and resulting reports. Cone health information and technology services is committed to the security of its assets, personnel, and. This guide provides updated guidance for the assessment of hitrust csf control requirements using the hitrust csf control maturity model,. The following is a library of free information security policy templates that map to the hitrust common security framework, which in turn maps to a. We’ve outlined the requirements of hitrust policies and procedures, the audit process surrounding the advanced paper exercise, and what you can do to.
We’ve outlined the requirements of hitrust policies and procedures, the audit process surrounding the advanced paper exercise, and what you can do to. The following is a library of free information security policy templates that map to the hitrust common security framework, which in turn maps to a. Cone health information and technology services is committed to the security of its assets, personnel, and. This checklist is designed to help ensure the consistency and quality of hitrust validated assessments and resulting reports. This guide provides updated guidance for the assessment of hitrust csf control requirements using the hitrust csf control maturity model,.
Hitrust Policy Templates
Cone health information and technology services is committed to the security of its assets, personnel, and. This checklist is designed to help ensure the consistency and quality of hitrust validated assessments and resulting reports. We’ve outlined the requirements of hitrust policies and procedures, the audit process surrounding the advanced paper exercise, and what you can do to. The following is.
Hitrust Policy Templates
We’ve outlined the requirements of hitrust policies and procedures, the audit process surrounding the advanced paper exercise, and what you can do to. This checklist is designed to help ensure the consistency and quality of hitrust validated assessments and resulting reports. This guide provides updated guidance for the assessment of hitrust csf control requirements using the hitrust csf control maturity.
Hitrust Policy Templates
We’ve outlined the requirements of hitrust policies and procedures, the audit process surrounding the advanced paper exercise, and what you can do to. The following is a library of free information security policy templates that map to the hitrust common security framework, which in turn maps to a. This checklist is designed to help ensure the consistency and quality of.
Hitrust Policy Templates
Cone health information and technology services is committed to the security of its assets, personnel, and. We’ve outlined the requirements of hitrust policies and procedures, the audit process surrounding the advanced paper exercise, and what you can do to. This guide provides updated guidance for the assessment of hitrust csf control requirements using the hitrust csf control maturity model,. This.
Hitrust Policy Templates
The following is a library of free information security policy templates that map to the hitrust common security framework, which in turn maps to a. This checklist is designed to help ensure the consistency and quality of hitrust validated assessments and resulting reports. Cone health information and technology services is committed to the security of its assets, personnel, and. We’ve.
Hitrust Policy Templates
This checklist is designed to help ensure the consistency and quality of hitrust validated assessments and resulting reports. The following is a library of free information security policy templates that map to the hitrust common security framework, which in turn maps to a. This guide provides updated guidance for the assessment of hitrust csf control requirements using the hitrust csf.
Hitrust Policy Templates
Cone health information and technology services is committed to the security of its assets, personnel, and. This checklist is designed to help ensure the consistency and quality of hitrust validated assessments and resulting reports. This guide provides updated guidance for the assessment of hitrust csf control requirements using the hitrust csf control maturity model,. The following is a library of.
HITRUST Policies Information Security Risk Management Procedure PDF
The following is a library of free information security policy templates that map to the hitrust common security framework, which in turn maps to a. This guide provides updated guidance for the assessment of hitrust csf control requirements using the hitrust csf control maturity model,. This checklist is designed to help ensure the consistency and quality of hitrust validated assessments.
Hitrust Policy Templates
The following is a library of free information security policy templates that map to the hitrust common security framework, which in turn maps to a. Cone health information and technology services is committed to the security of its assets, personnel, and. We’ve outlined the requirements of hitrust policies and procedures, the audit process surrounding the advanced paper exercise, and what.
Hitrust Policy Templates
We’ve outlined the requirements of hitrust policies and procedures, the audit process surrounding the advanced paper exercise, and what you can do to. Cone health information and technology services is committed to the security of its assets, personnel, and. This checklist is designed to help ensure the consistency and quality of hitrust validated assessments and resulting reports. This guide provides.
We’ve Outlined The Requirements Of Hitrust Policies And Procedures, The Audit Process Surrounding The Advanced Paper Exercise, And What You Can Do To.
This guide provides updated guidance for the assessment of hitrust csf control requirements using the hitrust csf control maturity model,. This checklist is designed to help ensure the consistency and quality of hitrust validated assessments and resulting reports. The following is a library of free information security policy templates that map to the hitrust common security framework, which in turn maps to a. Cone health information and technology services is committed to the security of its assets, personnel, and.